PARTNER NEWSFEED
Discover our partner news
Stay up to date with what we have been doing with our partners, how we're working with them to help our customers and what our partner experts are saying.

Filter:
- Adobe
- AMD
- Apple
- AppSense
- Aruba
- ASUS
- Belkin
- Brother
- Bullitt
- CAT Phones
- Checkpoint
- Cisco
- Cisco (Featured)
- Cisco Energy Management
- Cisco Energy Management (Featured)
- Cisco>Cisco
- Citrix
- Clearswift
- Clearswift (Featured)
- Cloud
- Commvault
- COVID-19
- Cyber
- Dell
- Digital Workplace
- EMC
- EMC (Featured)
- EPOS
- Epson
- F5
- F5 (Featured)
- Featured-1
- Fortinet
- Hitachi (Featured)
- Hitachi Data Systems
- HP
- HP (featured)
- HP>HP Converged Systems (Featured)
- HP>HP PC
- HP>HP PC (Featured)
- HP>HP Print
- HP>HP Print (Featured)
- HPE
- HPE>HP 3Par Storage
- HPE>HP 3Par Storage (Featured)
- HPE>HP Converged Systems
- Hybrid Infrastructure
- Hypertec
- IBM
- IBM (Featured)
- IBM>IBM Business Analytics
- IBM>IBM Business Analytics (Featured)
- IBM>IBM Emergency Response Services
- IBM>IBM Emergency Response Services (Featured)
- IBM>IBM Mobile Device Management
- IBM>IBM Mobile Device Management (Featured)
- IBM>IBM Power 8 Systems
- IBM>IBM Power 8 Systems (Featured)
- IBM>IBM Smarter Storage
- IBM>IBM Smarter Storage (Featured)
- iiyama
- Industry
- Infrastructure
- Intel
- Ivanti
- Lenovo
- Lenovo>Lenovo Data Centre Group (DCG)
- Lenovo>PC
- LG
- Logitech
- Microsoft
- Microsoft (Featured)
- Mimecast
- Mimecast (Featured)
- MobileIron
- MobileIron (Featured)
- NEC
- NEC (Featured)
- NetApp
- NetApp (Featured)
- Nutaix
- Nutanix
- Nuvias & Riverbed
- Oracle
- Oracle (Featured)
- Oracle>Oracle Converged Infrastructure
- Oracle>Oracle Converged Infrastructure (Featured)
- Oracle>Oracle Systems Consolidation
- Oracle>Oracle Systems Consolidation (Featured)
- Palo Alto
- Philips
- Philips (Featured)
- Plantronics
- Polycom
- Product
- Product (Featured)
- Qlik
- Quest
- Recent-Home
- Red Hat
- Remote working
- RES
- RSA
- Samsung
- SanDisk
- SCC News
- Security
- Software
- Symantec
- Symantec (Featured)
- Toshiba
- Uncategorised
- Uncategorized
- VCE
- VCE (Featured)
- Veeam
- Veritas
- VMware
- VMWare (Featured)
- ZAGG
- Zebra
Using the hybrid cloud is much like streaming a movie on a home theatre system. Pulling the film from the cloud to your big screen TV, the home theatre experience marries the benefits of the public cloud with the comfort of not having to leave the house and overpay for popcorn. The hybrid cloud, with...
Check Point vSEC for Azure Stack seamlessly secures the hybrid-cloud
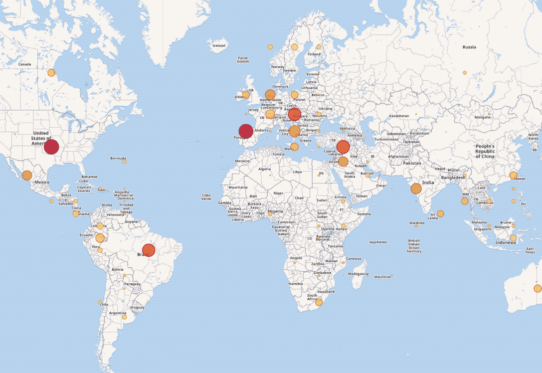
Check Point’s latest Global Threat Impact Index revealed that 28% of organisations globally were affected by the Roughted malvertising campaign during June. A large-scale malvertising campaign, RoughTed is used to deliver links to malicious websites and payloads such as scams, adware, exploit kits and ransomware. It began to spike in late May before continuing to...
June’s Most Wanted Malware: RoughTed Malvertising Campaign Impacts 28% of Organisations
As new security issues are revealed they have new names and sometimes keeping up and understanding this is a challenge! Here is SCC’s high level Jargon Buster to help you navigate the waters (plenty more fish references below). If you need specific help, contact [email protected]. Jargon Buster Cybercrime: Definition: “criminal activities carried out by means...
Phishing, Whaling, Zero Days – What does it mean?
XenApp and XenDesktop v6.5 was released in 2012 and since then, significant improvements on initially the products as well as the wider bundled functionality in later suites and versions. Later functionality now includes better enhancements that span the wider product sets that include XenMobile, SD-WAN (software defined WAN enhancing connectivity and network bandwidth optimisation) as...
Citrix XenApp and XenDesktop V6.5 Ends Security Patching at the End of 2017
2017 THE WORST YEAR FOR RANSOMWARE SCAMS WITH SOME EXPERTS PUTTING IT AT $4BN GLOBAL IMPACT Cyber risk modelling firm Cyence estimates the potential costs from the hack at $4 billion, while other groups predict losses would be in the hundreds of millions. The attack is likely to make 2017 the worst year for ransomware...
Cyber Crime, Ransomware, Malware, Phishing, Whaling – All Have One Thing in Common… Business Disruption
An event similar to the recent NHS attack could bring a university campus to its knees, says Graeme Stewart, Director of Public Sector, UK&I, Fortinet The recent WannaCry attacks that have proliferated throughout the NHS and other organisations across the globe prove that the disruption that ransomware can cause is not insignificant. Universities and other institutions...
Preventing a Cyber Attack on Campuses
Countering the Cyber Security Challenge The Fortinet Security Fabric provides a new, intelligent architectural approach to security that enables enterprises to see, control, integrate, and manage the security of their data across their entire organisation, even into the cloud. Read Now NSS Labs Breach Detection Systems Test: FortiSandbox with FortiClient Read Now Internal Segmentation Firewall...
Prevent Ransomware with the Fortinet Security Fabric
Attacks targeting and originating from IoT devices began grabbing news headlines toward the last quarter of 2016. Insecure IoT devices became the low-hanging fruit for threat actors to easily exploit. Some were even notoriously used as botnets to launch DDoS attacks against selected targets. For example, the infamous Mirai botnet exploited weak login vulnerabilities in...
FortiGuard Labs Telemetry – Roundup and Comparison of 2015 and 2016 IoT Threats
Cyber-attacks pose a significant threat to universities, every hour of every day. An attack can dramatically impact your organisation by causing disruption and compromising data, reducing and even shutting down normal service. It’s vital to protect what’s most important to you, for example sensitive data, intellectual property and research data. How sure are you that you’re protecting...
SCC and Fortinet join forces for UCISA 17
The healthcare industry continues to ride the digital wave to improve patient care and organisational efficiency while reducing costs. To do this, hospitals and health systems are relying on electronic health records (EHRs), the cloud, and the Internet of Things (IoT) more than ever. While these technologies are convenient, efficient, and enable a higher degree...
Infographic: Protecting Patient Data in Today’s Digital World
This Global Healthcare Threat Telemetry report examines the threat landscape of the global healthcare industry in Q4 2016. It is based on threat telemetry obtained by FortiGuard Labs’ research group from sensors located at 454 healthcare companies located in 50 countries around the globe. FortiGuard Labs, and its more than 200 researchers and analysts located...
FortiGuard Labs – Global Healthcare Threat Telemetry for Q4 2016

While there are many types of malware, including viruses, worms, Trojans, Spyware, Adware, and others, ransomware has gained the most notoriety over the last few years in part due to the popularity of crypto currency such as Bitcoin, as well its brazen ability to grind productivity to a complete halt.Simply put, ransomware is a considerable...