Securing Information in the New Digital Economy
The Situation
We are in the midst of a data breach epidemic, fueled by a lucrative information black market.
The perimeter security most IT organizations rely on has become largely ineffective. Almost 70% of security resources are focused on perimeter controls, but most exploited vulnerabilities are internal.
The result is a new hacker economy.
Hacking techniques and knowledge are widely accessible and attacks are common. Hacking-for-hire has allowed attackers to gain large rewards with a relatively small investment, allowing even novice users to participate.

How the Black Market Works
As stolen information ages, it loses value. Hackers keep their profits high by limiting supply, and staggering attacks over time.
Although security responses have a short-term impact, they unfortunately spur hacker innovation, resulting in an arms race.
The Solution
Think from the inside out. Better security controls for internal servers, applications, and databases combined with better monitoring and analysis of network traffic and server transactions can prevent these types of attacks.
Threats are External, Risks are Internal
Most organizations are focused on stopping malware after it’s installed:
They should be focused on how criminals gain access to install the malware in the first place.
There has been a 1600% increase in nine years.
82% of hackers use just three techniques.

Identity Risk is Serious
Many attackers use legitimate user credentials, and this makes detection and prevention difficult. These credentials are available on the black market.
76% of these attacks would fail, or the attackers would be forced to adapt, if people used strong passwords.
The Solution
Employ an inside-out strategy that assumes criminals are already on the network and protects sensitive information accordingly.
Database Threats are Real
Database and application security should go hand in hand.
Organizations aren’t paying enough attention to their internal vulnerabilities. For example, 42% of the most serious attacks against data are SQL injection attacks but only 38% of organizations have taken steps to prevent them.
62% of organizations either not or are unsure whether they are preventing SQL injection attacks.
The Solution
Good information governance and audit controls are required.
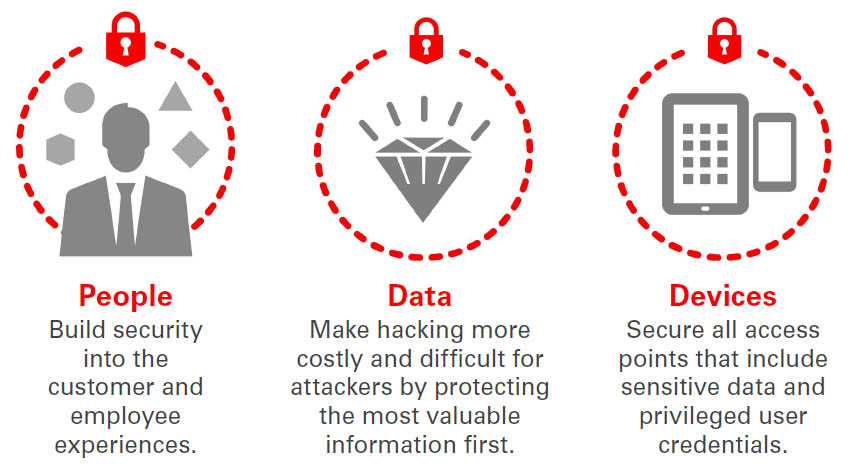
Thinking Inside Out
People, data, and devices are the new perimeter — the new front line in the battle for data security.
Learn more in the white paper, Securing Information in the New Digital Economy. Read it at www.oracle.com/goto/securinginfo