The Golden Hour of Cyber Security
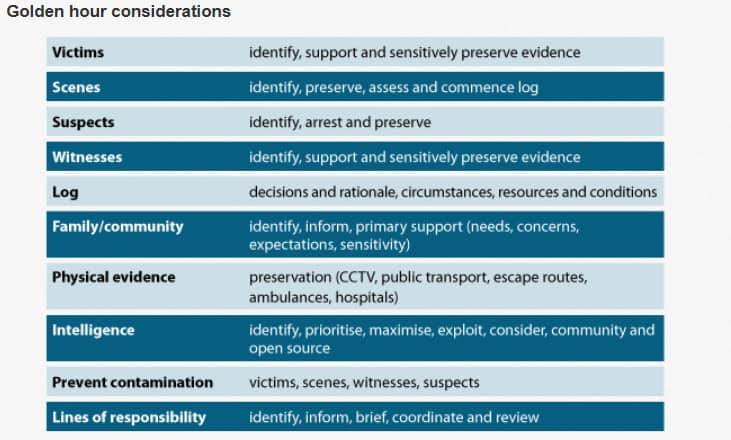 This approach can be rapidly and simply adopted by any organisation in any sector. While some of the headlines are specific to policing, it is vital that organisations have an agreed set of considerations such as building your incident response team and programme. Putting together a comprehensive incident response programme involves building a dedicated team that includes employees from all areas of your organisation. So not just people from the IT department, but also from HR, operations, public relations and legal departments, for example. You should also ensure a member of the board is part of the IR team. This guarantees that the right decision making occurs during the difficult and often traumatic environment all the team members find themselves in during a cyberattack. No one ever said this was going to be easy, but with such a high level, coordinated team the damage of an incident can be significantly limited. 3. Ask yourself some questions To set your structure, you need to ask questions of your organisation. If we take the Golden Hour considerations as a guideline, these questions would include: Lines of responsibility
This approach can be rapidly and simply adopted by any organisation in any sector. While some of the headlines are specific to policing, it is vital that organisations have an agreed set of considerations such as building your incident response team and programme. Putting together a comprehensive incident response programme involves building a dedicated team that includes employees from all areas of your organisation. So not just people from the IT department, but also from HR, operations, public relations and legal departments, for example. You should also ensure a member of the board is part of the IR team. This guarantees that the right decision making occurs during the difficult and often traumatic environment all the team members find themselves in during a cyberattack. No one ever said this was going to be easy, but with such a high level, coordinated team the damage of an incident can be significantly limited. 3. Ask yourself some questions To set your structure, you need to ask questions of your organisation. If we take the Golden Hour considerations as a guideline, these questions would include: Lines of responsibility
- Technology and information security. This would be the Head of IT and the CISO, for example. Your technical people will know the network environment and can help dig into the details in system logs, network packet captures, vulnerability scanner reports. Your CISO will already be conversant with issues around information security, data protection and existing compliance measures.
- Board member. This could be your head of operations.
- Incident response coordinator. You will need to decide who is responsible for ongoing management of the team and incidents.
- Media relations. Your PR or marketing department will need to take control of all media relations.
- Forensic analyst. A forensics expert can be internal to the company or an outside adviser.
- Legal. Your own corporate lawyer or an outside law firm – someone who would help you to navigate the legal issues following a breach.
Victims
- Who will a breach impact?
- The impact could involve loss of revenue, theft of data or damage to reputation
Log – Incident Response Blueprint How will you record what has happened? There has been recent market growth in IRP/SOAR platforms that orchestrate and automate incident response processes. While these platforms quickly and easily integrate your existing security and IT investments, providing instant actions for security alerts, they’re not cheap. An alternative therefore is to create an “in-house” written incident response blueprint that follows a logical pattern of who, what, when, why and how as the incident unfolds. The blueprint document is essential to ensure that panic doesn’t spread across the team as each member starts to comprehend the impact of the incident. Often, it’s a daunting experience so good, clear, cool decision making is critical to ensure the correct steps are taken to limit the damage of the breach. With your blueprint you can respond in a clear, logical way and ensure that legally you as an organisation are adhering to all required security industry legislations. Community How and when will you inform your customers/partners/shareholders about what has happened? Intelligence
- What can you discover from your event log?
- What other sources of intelligence do you have?
4. Conduct a trial run With fire drills standard in all public buildings and compliance training often focused on real-life scenarios, it makes sense for organisations to take the same approach to cyber incidents. At a basic level this could involve a simulation where members of the immediate security team rehearse their actions, or it might involve the entire company. While this could disrupt business for an hour, a well-prepared team can save an organisation significant time and money in the event of a real cyber attack. There is also the added benefit of being able to uncover and rectify process errors or knowledge gaps in a safe environment. 5. Be your own best warning system Give yourself the best possible opportunity for predicting a cyber attack by occasionally rehearsing your Golden Hour attack simulation. Here’s our top three tips:
- Be process-orientated – Technology and tools are important, but your technology will not fix an issue that’s rooted in process.
- Active monitoring – You want people patrolling your network who have context on your business and what threats exist.
- Creating a culture of awareness – Cyber security shouldn’t be top-down or bottom-up, it should be an organisation-wide responsibility.
Related event: SCC is playing a key role at this years’ CBI’s Cyber Security Conference on September 12th in London, which brings together business leaders and the UK’s foremost industry experts on cyber security. From the latest National Cyber Security Centre intel to insight from the World Economic Forum to how you can avoid a PR disaster in the event of a cyber attack, various experts will provide cutting-edge insight and practical solutions to enable you to plan your strategy with confidence.